Telecommute Safely With Shields Up Against Cyberattacks
Cybercriminals are always looking to take advantage of slip-ups in online behaviour. Follow these simple cyber hygiene rules to avoid falling victim to two common cyberattacks amid the need for information in the COVID-19 outbreak.

While healthcare workers and governments worldwide are busy battling the COVID-19 outbreak, an old foe continues to lurk: cyberattack attempts on people seeking information from trusted sources.
In just one week, more than 18 million COVID-19-related malware and phishing emails were detected daily, Google reported in April. That’s on top of 240 million daily spam messages relating to the coronavirus.
With many of us now in telecommuting mode, working on our personal devices and email systems, the exposure to cyberattacks is higher. Cyberattacks can infiltrate a network and infect everyone linked to it.
Fake apps
How the attack targets you
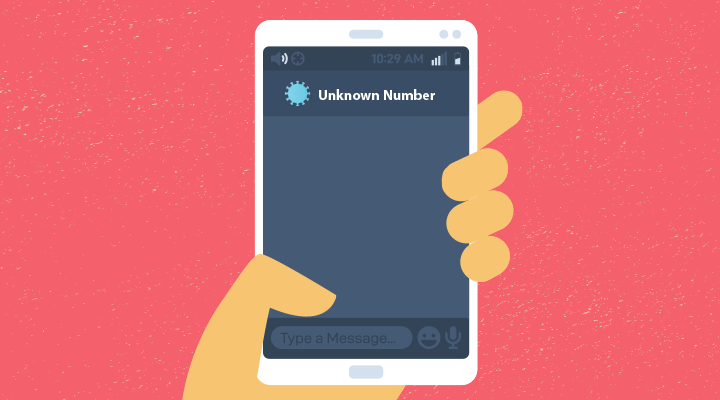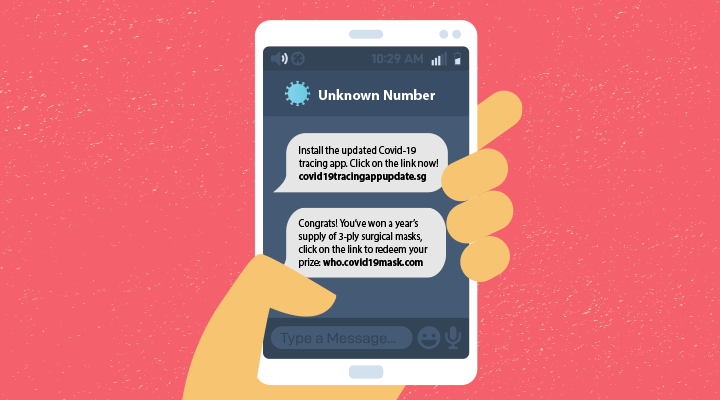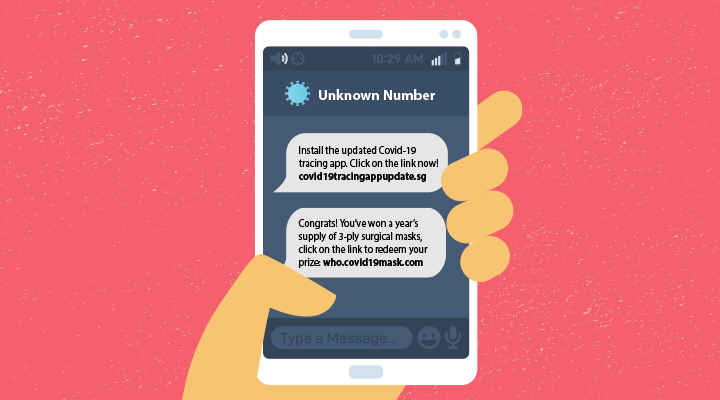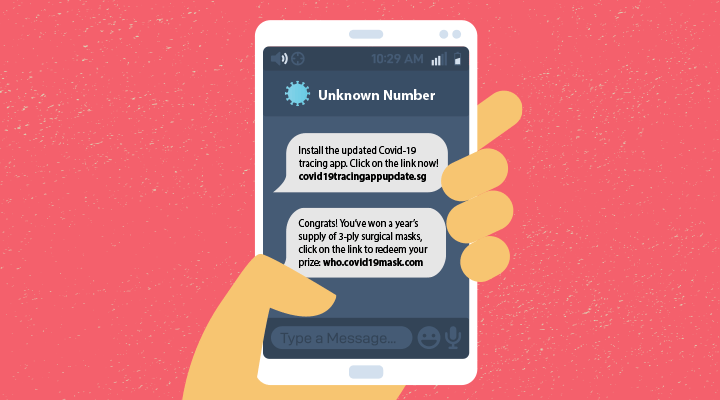
Links in text messages entice you to install apps claiming to track COVID-19. Phishing campaigns disguise themselves as official communications from trusted sources such as the World Health Organization or Ministry of Health. These messages may come complete with the authority’s brand and trademark. Opening the links or attachments will download malware onto your devices.
What the attack does
As you launch the app more frequently, the app will request additional access to your photos, media, files, device location, and permission to take pictures and record videos.
Cybercriminals can then take control of your devices and demand payment from you to unlock the device or steal your identity by logging keystrokes to access personal information and financial data.
How to defend yourself
- Download mobile apps only from official app stores. Avoid downloading apps from unofficial sources or links sent via text even if the application appears in an official app store.
- Keep your devices’ Operating System versions up-to-date.
- Scrutinise the links or attachments in all emails, even those that appear to come from trusted sources.
Phishing emails

How the attack targets you
Phishing emails impersonate medical specialists sharing news on the COVID-19 situation, and entice you to click on attractive links or attachments.
Other phishing emails may take on the form of emails sent out by your organisation’s senior management or your bosses.
What the attack does
Besides phishing for personal data, phishing emails trick you into making fraudulent fund transfers for vaccine information or official COVID-19-related documents. Common file types of malicious attachments are .pdf, .mp4 and .docx files.
Phishing emails may contain links directing you to malicious websites created by cybercriminals.
Visiting these websites can trigger the download of malicious files. If your device becomes infected, cybercriminals can gain unauthorised access to the infected system remotely and steal the personal credentials of everyone connected to the network.
How to defend yourself
- Do not click on any suspicious links in the email body. Verify the suspicious links with the sender to be safe.
- Do not open any suspicious attachments in the email. Verify the suspicious attachments with the sender to be safe.
- Do not reply to any spam emails.
- Report all spam emails.
- Refer directly to official sources, such as the Ministry of Health website, for trustworthy and legitimate information on the COVID-19 situation.
Now that you know how to better shield yourself from cyberattacks, be sure to share these tips with your friends and family so we can all avoid getting reeled in by cybercrime.
- POSTED ON
May 8, 2020
- TEXT BY
Tuber
GovTech








