Instruction Manual: All About Personal Data Protection

Jargon Watch
Public Service Jargon
KYC= Know Your Customer. KYC is a series of authenticating processes by financial institutions, which requires collecting customers’ personal information and tracking their transaction patterns to identify the risk of fraud, money laundering and corruption activities. The processes must comply with data protection laws.
PII= Personally Identifiable Information. PII refers to any (digital) information that can be used to decipher the owner’s identity and is protected under data privacy law (e.g., email addresses, contact numbers, credit card information, mailing addresses).
Tech Jargon
Cryptojacking= The unauthorised use or takeover of a computer to mine cryptocurrency (e.g., Bitcoin). This happens when the victim clicks a malicious link or uses an unsecure network. The hacker may also hide the mining program in online ads to infect websites.
Ransomware= Malware that locks the victim’s access to his or her own files, with threats that the data will remain locked unless the ransom demand (usually for money) is met. However, you should never agree to the ransom as there is no guarantee you will get your access restored.
Say It Like This
Privacy: Americans tend to say “pry-va-cy” (using the first syllable sound in “primate”) while the British prefer “pree-va-cy” (similar to “privy”).
Ask A Pro
Going Beyond Data Protection

A Q&A with Mr Lam Chee Kin, DBS Managing Director and Group Head of Legal, Compliance and Secretariat. He is also a member of the Data Protection Advisory Committee of Singapore.
Q: What is the value in ensuring customers' personal data protection?
The use of data enables the digitalisation of business and brings competitive advantages. Using data well – for business insights, strategy, marketing, risk management and so on – is one of the things that underpins the digital revolution.
It follows that the appropriate protection and security of data, and the ability to demonstrate that to customers, will similarly be a competitive advantage.
But if the prize you want is customer confidence and trust, just implementing the law, e.g., according to the Personal Data Protection Act (PDPA), will not win you the prize. For customer confidence, more must be done.
Data protection has a correlation with cybersecurity. Beyond obtaining consent, the security regime must be considered too. If a hacker can get into your system, you are not really protecting your customer data.
The moment your customers feel that you cannot protect, secure or use data responsibly, your ability to harness the advantages of data will be fatally compromised.
Q: What are some warning signals that data has been compromised?
There is a difference between an individual’s warning signals, and warning signals for a company or organisation. On the individual level, one sign is getting a lot of calls from moneylenders, tuition teachers and so on.
From an institutional perspective, it depends on what the institution decides to measure. For example, it is a fairly safe guess that if somebody resigns, that person may try to take a lot of information out from the organisation. So DBS looks at the behaviour of people who have resigned quite carefully, among other things.
Q: The PDPA requires a data protection officer to be appointed in every organisation. How should different types of organisations do this to ensure data protection?
DBS has a single point of contact for data protection, which is more streamlined for engaging with our regulators and our staff. We keep a single view and approach for data governance and implement that for all our countries where we have a footprint.
The downside risk of DBS making a mistake of data protection would be much higher than mistakes by a smaller organisation. Because DBS is responsible for much more customer information, we can and should spend accordingly on having a centralised data protection officer.
But this does not mean smaller businesses can avoid ensuring data protection. Many small businesses have massive amounts of customer data. Tuition teachers, for example, hold a lot of customer information. A karaoke lounge has memberships, customer tracking and so on, and is very different from a provision shop where the customers just walk in.
With any business or organisation, there is a need to think about the type of business being done, and how to build an appropriate data protection structure for it.
Got a question or topic you want answered by a pro? Send your suggestions to psd_challenge@psd.gov.sg
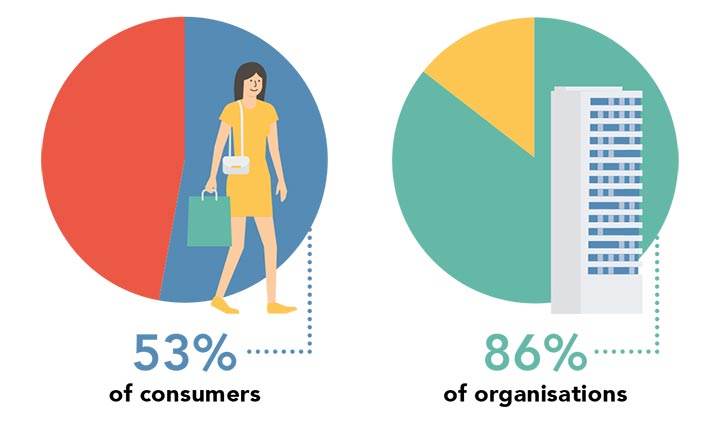
In Numbers
A look at people’s awareness of the Personal Data Protection Act (PDPA) in Singapore.

Get Wired
Good habits to maintain data privacy
Protect yourself by taking these steps
In the cloud: where does your data go?
Only agree to share personal information on the online platforms you know well. For example, when prompted by their mobile device, many people opt to sync photos and documents to the cloud. Doing so means that the mobile device is no longer the only point of access to the data. Make sure you are familiar with how to retrieve, delete or restrict access to your files in the cloud once they are synced.
Protect all types of personal data
Creative phishing ploys are on the rise. For example, users may be asked to change their secondary email address or share an authentication code sent to their phones. Sharing this information is just as dangerous as revealing passwords – it allows the hacker to “prove” access to the user’s back-up email address or phone number, potentially allowing them to reset the victim’s password and log in.
Know how to opt out
- Add your phone number to the Do Not Call registry
- Got an unwanted telemarketing call? Tell the person on the line that you wish to be taken off all current and future call lists from that company.
- For unwanted promotional emails, find the unsubscribe option (usually in small print at the end of the email) and follow the instructions to unsubscribe.
- POSTED ON
Sep 24, 2018
- TEXT BY
Chia Soong Ming
-
Work Better
Instruction Manual: 5G And Mobile Connectivity
-
Work Better
Instruction Manual February 2018









